Windows 10 Steals Your Internet Bandwidth to Send Updates to Others, Disable It Here
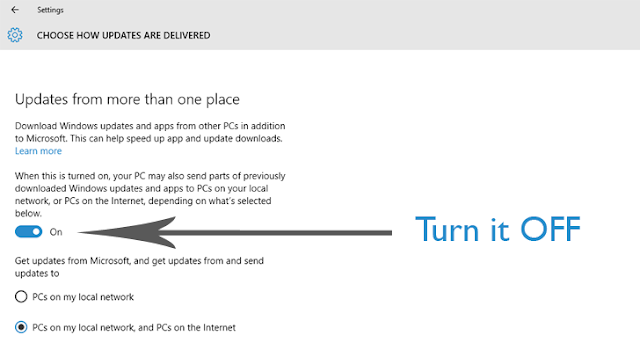
After installing Windows 10, Feeling like your Internet Bandwidth is dropping away? Windows 10 is stealing your network bandwidth. Along with the privacy features related to Wi-Fi Sense, Windows 10 users should check for another hidden by default feature that uses your network bandwidth to share updates with other Windows 10 users across the Internet. Microsoft launched Windows 10 on July 29 and offered a free upgrade to Windows 7,8 and 8.1 users, and for anyone who wants to download it. But, handling millions of simultaneous 3.5GB downloads is quite difficult for the company. So, in order to cope up with the issue, Microsoft has baked a new feature into its latest desktop operating system that uses the torrent-style approach to obtain software updates, allowing Windows 10 users to download updates from other users. Windows 10 is Stealing your Internet Bandwidth The feature, known as Windows Update Delivery Optimization (WUDO), is initially designed to help users get faster softwar